idp.generic Virus Removal Guide [Avast Antivirus]
Computer users receive an infection warning and an IDP.generic virus when using AVG or Avast Antivirus. Read our removal guide.
Table of Contents
What Is idp.generic?
This could indicate an attack on malicious software because AVG or Avast software appears with the following message:
“One of your programs behaves strangely, which can be a sign of malware.” Path: C: Windows System cd.exe Infection: PGI.Generic “.
Some people face this infection even when using Avast’s antivirus software.
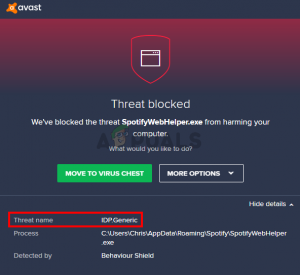
Generally, a common IDP infection indicates that some elements of identification recognition have detected the infection.
Generally, it is a common file that has been recognized. This could also be false positively, which could be due to some obsolete definitions. For the most part, these bugs or infections can easily be corrected by preventive measures.
How can I resolve and remove the “IDP.Generic” warning?
1. Update AVG / Avast Update
“IDP.Generic” is a known issue in programs like AVG and Avast Antivirus. The easiest way to fix this problem is to update AVG or Avast Antivirus software to the latest version. You can do this:
- Open the AVG software. Go to the menu bar and open the Settings tab.
- Here you can click the “Update” button. Try updating the virus definition and the program.
- Restart the computer to see if the problem is resolved or not.
2.Change of Antivirus
If the problem persists, you can not use the AVG software or antivirus software that is causing the problem.
If you have problems with your computer, you should try the Advanced. CNET describes it as “Swiss Army Knife for the Computer.” After downloading, you will receive a series of optimization tools that include an uninstaller, one-click registry fixes, defragmentation programs, and more.
4.Try Switching To VirusTotal
Another solution is to install and use VirusTotal, a software service that allows you to analyze suspicious files and URLs. The VirusTotal software service also allows for faster detection of viruses, trojans, worms and all types of malware detected by antivirus.
After installing VirusTotal software on your system, follow these steps:
- Click “Browse.” Copy the following lines in the File Name field:
- C: Windows System32 rundll32.exe
- Click “Open.”
- Then select the Send File icon at the bottom of the VirusTotal page.
Note: If you receive a message that the files have already been sent, you can click on “Re-analysis.”
- Finish the scan.
5.Java Update
One of the main causes of the “IDP.Generic” problem could be that Java is not being updated on the computer system.
Previous versions often have vulnerabilities that allow malicious applications or software to infect the entire system. Therefore, to remove and update an earlier version of Java components, we recommend that you do the following:
- Download the latest version of Java Runtime Environment 7 Update 5 and save it to your desktop.
- Go to “Java SE 7 Update 5” and select “Download JRE.” Click Accept license agreement.
- Click this link to download “Windows x86 Offline” and save it to your desktop.
- Go to Start> Settings> Control Panel. Click “Add or Remove Programs” and remove all previous versions of Java.
- Restart the computer when all Java components have been completely removed.
- Now click “jre-7u5-windows-i586” on the desktop to install the latest version of Java.
For more protection, consider installing the Malwarebytes Anti-Malware software, an on-demand scanner that scans the entire malware system. You can update it each week and make quick checks. Buy a license to take advantage of the additional features of this program.
idp.generic False Positive
Most likely, IDP.Generic is in different circumstances, even with a false positive result(source).
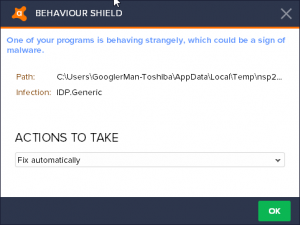
Some people have VirusTotal software to diagnose the problem by checking all of the relevant HashCheck files, but none of the AVG programs have encountered problems, not even Avast’s anti-virus software.
Here’s how to do it:
- Try updating Avast if you are using a previous version.
- Reinstall HashCheck
- Otherwise, you can temporarily disable Avast software.
The idp.generic Infection
Many people do not realize that whenever they use their computer to scan the Internet or search for their emails, the background is much more. There are many hidden applications that are never observed for the most part.
When viewing the list of these applications, unknown names are displayed. They come and go when they need it, and they can run a lot at any time. Some perform simple functions in the PC operating system that are not visible.
Others are complex and worthwhile programs running on our screens. Each one of them exists together, divides the memory of the device and establishes continuous contact with each other as an electronic digital ecosystem.
Hackers or intruders use all these hidden applications on their laptop or computer, hiding their malicious software, also known as malware, and therefore does not even recognize them. The first task of the attacker is to provide the victim with the adware and spyware.
Personal computer The usual tactic is to let the end users do it themselves. Among other things, online hackers can do so simply by sending an e-mail with a legal document. However, the document does not seem suspicious, but in fact, it contains a malicious computer code.
In the video, they behave that way. Liam plays the role of victim, so he’s connected to your email early in the morning and gets new.
He then received an e-mail about his open health insurance registration. Although I do not know who the sender is, I will open this attachment, upload the document and open the document with a trap. An error message is displayed.
However, the target does not understand that malware is also loaded quietly into the computer system simply by clicking on it.
Important Note
If the victim opens this document, the secret code of the computer’s internal program will run on your computer without realizing it and will connect to your computer with the software that launches the hacker.
Such privacy programs allow a catastrophic invasion beyond the line in which an attacker can spy or annoy at will.
For example, you can also capture screenshots of your computer and locate all lines with the help of a keylogger. They show how the victim can access his e-mail and retrieve his username and password by entering it with a password.
In addition, by activating a camera, they can also export video and see exactly how their victim appears without knowing.

